I did not plan on writing a series about hardening Django on EC2.
It actually started before I deployed anything.
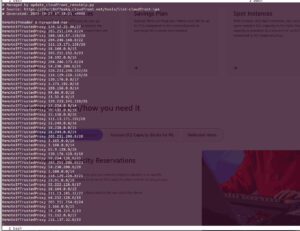
I spent enough years setting up Linux servers that I developed a reflex: whenever I build a new machine, I install a firewall, lock down SSH, and turn on Fail2ban almost automatically. Ive watched Fail2ban quietly block thousands of bad SSH attempts over the years sometimes within minutes of bringing a server online.
So when I began preparing to deploy Django on EC2, I had this moment of realization: Wait why am I not treating Django the same way I treat SSH?
If Fail2ban protects your shell, why cannot it protect your admin panel? Your login pages? Your API endpoints?
And that thought plus a quick skim through some logs confirmed it. Even before opening Django to the public, I knew I wanted the same level of automatic, server-level protection that had saved me countless times on bare Linux.
This series grew from that mindset: bringing the power of traditional Linux hardening the stuff that just works into the Django world. These posts are not theory; they are the actual steps I followed to prepare my Django deployment before it ever went live.
If deploying Django on EC2 especially behind CloudFront or Apache, I think you will find these guides helpful.